Tag: cyber security
Hikvision embarks on European cyber security roadshow
Hikvision has set out on a European roadshow with the aim of raising awareness on key cyber security concerns and giving tips on how...
Dahua & Pepper partner on full-stack cyber security
Dahua Technology has recently entered into a strategic partnership with Pepper, an IoT platform-as-a-service, to allow the integration of its intelligent solutions into Dahua...
AI is Fundamental to the Future of Cyber Security According to...
Nearly 70% are looking to implement AI in the next five years, as Senseon Pro is launched to help SMEs combat the complexity of...
Industrial cyber security strategies need a radical rethink
Despite the imminent danger, cyber security investment within the ICS market is severely lagging, expected to barely cross the US$2 billion mark by 2025,...
Industrial cyber security strategies need a radical rethink
Despite the imminent danger, cyber security investment within the ICS market is severely lagging, expected to barely cross the US$2 billion mark by 2025,...
Cyber security demands a holistic informative approach
Jon Isaacson, Product Manager, Systems, at Indigovision says that cyber security, or ‘the security of your security’ as some in the industry are calling...
Cisco partners with Colombian government on cyber security
Cisco and Colombian President Ivan Duque Marquez have announced joint efforts to fund and develop secure digital solutions addressing key social and economic goals...
Trend Micro announces the launch of managed detection and response (MDR)...
Trend Micro Incorporated, a global leader in cybersecurity solutions, recently held its annual Channel Partner Day event in Gangtok, Sikkim. The three-day event, attended...
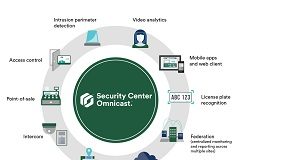
Omnicast receives highest level UL cyber security certification
The Genetec VMS Security Center Omnicast has received the UL 2900-2-3 Level 3 cyber security certification. A long-standing advocate for cyber security and the...
Focus on a total security approach – beyond cyber security alone
Cyber attacks targeting IoT devices and consequently video systems as well are growing more frequent at an unprecedented rate. The things users should consider...