A hacker who tested 16 smart security systems, connected smoke alarms and thermostats found weaknesses in every single one, according to a report by KGO-TV. “We could intercept the video stream to your cameras,” Colby Moore, a professional hacker, told 7 On Your Side. “We could watch what you were doing at all times. We could even shut off your video camera. We could sometimes turn off your home alarm system.” Moore is part of the security team at Redwood City, Calif.-based Synack, a provider of cybersecurity solutions. The company purchased cameras, home automation controllers, thermostats and smoke detectors as part of its study.
“So on all 16 devices, it took about 20 minutes to do what we call rooting the device, and that means we can run our own code on it, and manipulate the device any way we want,” Moore said. Moore can hack into a thermostat and smoke detector then use them as an entry into other devices in your home, according to the news report. “They can then kind of pivot from that fire alarm to compromise other cameras, other computer systems,” he said.
Through a Nest thermostat, another hacker took control of the lights and electronically imprinted his logo on the device. A third hacker cracked a password by running a program with every imaginable password combination until it spit out the network key. “Once you can get the network key, it’s as if you were in the person’s house, because you’re on their network,” Jeremy Hajek, a professor of the Illinois Institute of Technology, told 7 On Your Side.
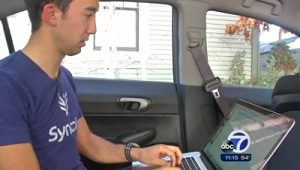
Weak passwords are one of the main reasons why hackers have it so easy. Another is lack of encryption which requires a secret key or password to read it. “One of the reasons security is so bad is that a lot of these people that are designing these products aren’t security people,” Moore said. “They don’t have the security background to efficiently design a secure product.” 7 On Your Side went with Moore while he hacked into a home in Menlo Park, Calif., near San Francisco.
He did it all from his car outside the home, but he could be anywhere, hacking into a home in the Bay Area and then sending someone else to carry out the burglary. “We do what we call reverse engineering,” Moore said. “We reverse engineer the device and just determined how it worked. Once you figure out how it works, you can figure out how you can compromise it.” Reverse engineering can take weeks, but once that happens the rest can be done in seconds. It took him less than 30 seconds to gain access to the camera inside the home. Then he disables the alarm in 12 seconds.
According to the news report, end users can protect themselves by hardwiring as many devices as possible. The report also suggested to set up push alerts to be notified when any wireless device is offline, and any data sent to cloud should use a secure connection.











