With security threats on the rise, LILIN Americas is answering the call by introducing an advanced yet easy-to-install Access Control System for monitoring entry to a building, resulting in a safer environment for personnel and assets. When integrated with other platforms such as IP cameras, fire alarms, and sensors, the system provides a layered security approach that significantly enhances peace-of-mind and acts as a deterrent for
Designed to work seamlessly together, the building blocks of the LILIN Access Control System are:
• TCP/IP Single Door RFID Card Reader and PIN Controller (AR2015)
• PoE Relay Box (ARR2010E)
• TCP/IP Multi- and Single-door Control Panels (AC1082, ACW10120)
• AC/DC Power Supply (PMH-PSU330)
• LILIN Access Control Software
Various combinations of the hardware platform are installed depending on the three available configurations — Standalone mode, Standalone with PoE mode, or Mixed mode. By using only what hardware they need, LILIN customers can significantly reduce installation time and total cost of ownership, while achieving operational efficiencies and gaining greater visibility into their security environment.
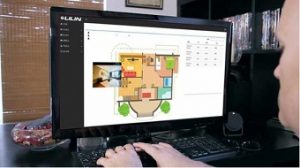
Standalone and Standalone with PoE modes are targeted primarily at small commercial and select residential applications, while Mixed mode is recommended for enterprise-level deployments with Wiegand readers and integrates with LILIN’s advanced Navigator series recording solutions. The Access Control web-based software provides a gateway to unified access control, enabling administrators to manage all of their security devices on a single interface. For example, the software’s multi-level mapping feature lets users monitor up to three live cameras at each intrusion area, while logging the event in real time. If an alarm event occurs, the administrator is sent an E-mail notification and the software brings up live video on the screen for viewing.
LILIN Access Control Software enables logged events to be fully searchable for later analysis, a process that is made easier by the software’s ability to display individual logs with a snapshot of the person involved and employee information, if available, along with recorded surveillance video. Tampering with a card reader, forcing open a door, insufficient permissions, or propping open a door for an extended period of time are all events that would set off an alarm.












